Financial institutions in the United States and Europe are on guard for a potential cyberattack as the war rages in Ukraine, Several Ukrainian banks have already experienced such attacks, and continuation of the war could turn Russian hackers’ sights on Western governments and financial institutions.
Criminals, cyber gangs and nation-states have long targeted financial institutions for monetary gain, so banks and credit unions aren’t new to the idea of cybersecurity and already have controls in place. Yet the escalation of the war in Ukraine and further sanctions from the U.S. and other countries could trigger direct state-backed attacks that financial institutions haven’t faced before.
Unlike random, financially-motivated ransomware attacks, these geopolitical attacks are intended to cause disruption and chaos, says Bill Conner, CEO, SonicWall, in an interview with The Financial Brand. Such attacks can include distributed denial-of-service (DDoS) that overwhelm targets with fake traffic, wiper malware that destroys data or systems, and vulnerability exploitation to disrupt critical infrastructure, services, supplies and communications. Many of these attacks could temporarily cripple a bank or credit union and its customers.
Threat Alert:
The potential for a 'full-on' cyberattack from a hacking powerhouse is very real.
DDoS attacks flood a network with so much traffic that it cannot operate normally, making it difficult for financial institutions as specific systems suddenly become unavailable or work intermittently, Conner explains. “Critical business data would be inaccessible. Websites would be down.”
Several Ukrainian banks were already hit with suspected DDoS attacks in the days leading up to the invasion.
Unlock the potential of your financial institution's digital future with Arriba Advisors. Chart a course for growth, value and superior customer experiences. This webinar from Veeam will detail the value of working together across your organization to be better prepared in cyber defense and response readiness. Read More about How Banks Are Fortifying Their Data Against Increasing Cyber Threats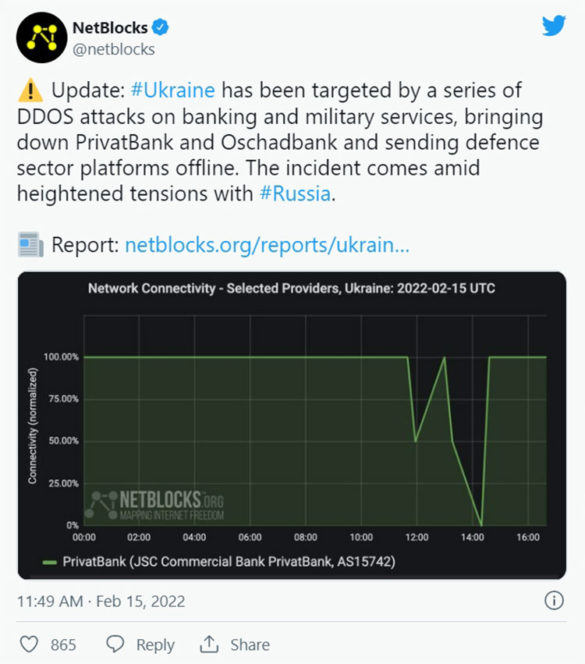

Are You Ready for a Digital Transformation?

How Banks Are Fortifying Their Data Against Increasing Cyber Threats
A New Level of Threat for Banking
Russian hackers are especially adept at “patriotic hacking,” and U.S. banks “have never had to withstand a full-on, all-in cyberattack by a nation as powerful in cyberspace as the Russians,” states Herbert Lin, senior research scholar at Stanford University’s Center for International Security and Cooperation, in The Atlantic.
George Kurtz, CEO of CrowdStrike, a company that works with most of the largest U.S. banks, told CNBC that wiper viruses are especially concerning because they can destroy data and disable operating systems. Data wiping malware has already been found on hundreds of computers in Ukraine.
As noted, cyberattacks were launched in Ukraine even before the first missiles hit. The real risk is how far they spread and whether Russia will intentionally target European and U.S. institutions.
Past cyberattacks in Ukraine have spread internationally before, such as the “NotPetya” ransomware attack in 2017. It started in Ukraine and eventually spread around the world, causing more than $300 million in global damages, according to Wired. The CIA later concluded that the Russian military was behind the attack.
Read More:
- Banking and Payments CX Jeopardized By Surge In Digital Fraud
- The Role Banks & Credit Unions Must Play to Prevent Human Trafficking
What a Russian Attack on U.S. Institutions Might Look Like
A worst-case scenario could potentially spur severe and unknown disruption for financial institutions. Federal Reserve chairman Jerome Powell said at a briefing in December 2021 that a cyberattack taking down a major financial institution or financial market utility would be a “significant financial stability risk that we haven’t actually faced yet.”
Lock the Door... and Set the Alarm:
It's doubtful any financial network or institution is impregnable to digital attack, so early detection and quick response are key.
In the leadup to the war between Russia and Ukraine, executives with Citigroup, JPMorgan Chase and Wells Fargo met with U.S. government officials to discuss the cyber threat. During a press briefing, Anne Neuberger, Deputy National Security Advisor for Cyber and Emerging Technology, said that the government was preparing for contingencies by “sharing sensitive information, encouraging private sector owners and operators to do the work they need to do to lock their digital doors. Essentially do the equivalent of putting on an alarm so one can rapidly identify if there is an intruder and quickly contain and respond.”
Before the invasions began, some Ukrainians reported issues with ATMs and banking services at State Savings Bank, PrivatBank, and Oschadbank. Ukrainian Strategic Communications Center and Information Security confirmed on Feb. 15 that PrivatBank was under attack leading to issues with payments and banking applications.
While no funds were stolen, cyber attacks in the beleaguered country were expected to escalate as the situation does, and many analysts say it’s a matter of how far Russia will take such cyber disruption. Russia is home to some of the most infamous criminal hackers, which have been blamed for DDoS attacks in Crimea in 2008 and 2014 and for attacks on electrical substations that caused power outages in 2015 and 2016. Operatives from Russia, along with others from China and Iran, were suspected of breaking into U.S. utility computer systems in 2014.
Recognition and a Fast Response Are Critical
While experts and government officials remain concerned, the good news is that strong regulations in the banking industry mean many financial institutions already have cyber fraud safeguards in place. In addition, while cyberattacks can be highly disruptive and costly, they are usually temporary, unlike damages in a physical war. Security experts say early detection and fast response can mitigate the damages of such attacks.
“It’s easy to hear [cyberwar] and compare it to real war. But the reality is, most of the cyberattacks we’ve seen have been … largely reversible,” John Hultquist, vice president of intelligence analysis at Mandiant, told CNBC.
In February, Biden administration officials announced a “shields up” initiative to protect critical infrastructures like pipelines, hospitals, commercial aviation and banks. Yet, for obvious reasons, neither the U.S. government nor big banks have been very detailed about new security measures or defenses they are taking.
In the meantime, banks and credit unions should also strengthen their defenses against seemingly ordinary ransomware. While ransomware attacks are typically used for financial gain, they can also be used to create disruption and misdirection, says SonicWall’s Conner. In extreme cases, they can also be used to take down critical infrastructure and cause chaos, disruption and financial loss.
When it comes to protecting against the threat of geopolitical attacks, the best strategy is to be proactive, Conner states. “Financial institutions need to minimize their attack vectors and closely monitor their network activity for quick identification of any attack,” he said.
A more significant risk is a larger cyberwar and mass-scale cyberattacks against the U.S. electrical grid, which would disrupt the banking and payments system in the process. A joint report from the Department of Homeland Security and the FBI in 2018 claimed that Russian hackers had already gained access to computers in the power industry and obtained sensitive data like login information.