Nothing captures a consumer’s attention more than an urgent email from their bank warning them that their account has had a security breach. And that’s really the problem.
Scam emails used to be obvious and easy to identify. But in recent years, they have become so sophisticated and believable that even trained cybersecurity professionals can’t always identify what is or isn’t real. In many cases, criminals are now using security alerts and emails that look exactly like those sent from banks to capture customers’ login information.
Ever resourceful and innovative, criminals were quick to capitalize on rapid growth in digital banking during the pandemic, as consumers became more accustomed to dealing remotely with financial institutions. The threat not only undermines consumer confidence but complicates the job of communicating with customers.
Big Spike in Phony Emails
Phishing is simply a type of scam where an attacker uses fraudulent messages designed to trick the victim into revealing sensitive information. There are many variations buy most phishing attacks consist of a cleverly disguised email from a trusted source that asks a recipient to visit a website or app and log into their account. While phishing attacks are relatively simple, they are also highly effective, Sébastien Goutal, Chief Science Officer at Vade, tells The Financial Brand.
What Changed:
Wise to the potential that increased digital banking presents, criminals use ‘psychological leverage’ in their phony emails.
According to Vade’s Phisher’s Favorites Report for the first half of 2021, phishing attempts jumped significantly in mid 2021, rising 281% in May 2021 and another 284% in June. Of the top 25 most impersonated brands listed in the report, eight were financial institutions, which comprised 36% of the phishing URLs detected.
French financial services giant Crédit Agricole topped the list as the world’s most impersonated brands with 17,555 unique phishing URLs. Others included Las Banque Postale, PayPal, Chase, and Wells Fargo. HSBC, and Banque Populaire.

Send the Right Offers to the Right Consumers
Achieve a better return on your marketing investment. Leverage behavioral data and analytics to target the right customers with the best possible offers.
Read More about Send the Right Offers to the Right Consumers

Move the Needle from Attrition to Acquisition
Vericast’s 2024 Financial TrendWatch explores seven of today’s most critical financial services trends to provide a complete view of the current loyalty landscape.
Read More about Move the Needle from Attrition to Acquisition
Financial are a prime target for phishing because they are a good way to get consumers credentials and use them for a quick hit, observes Goutal. The criminals connect to the account, take it over and do a wire transfer.
Most phishing attacks use “psychological leverage” and compelling messages to lure victims into taking action, says Goutal. Common bank-related phishing emails often include notifications about account closures, low balances or opportunities. Unlike brute-force digital attacks, the intent of phishing is to discretely capture information, access an account and get away with funds before the victim even knows anything has happened.
( Read More: Make Digital Banking Seamless and Secure or Consumers Will Switch )
Baiting with Bank Brands
While phishing isn’t a new tactic, it has become more widespread, and criminals are increasingly using bank brands as the “bait.” According to the Q1 2021 Brand Phishing Report by Check Point Research, banking has now surpassed retail as the number three industry for hackers to acquire and misuse customer’s personal information.
Check Points lists Microsoft as the brand most targeted by phishing (39% of all global attacks). Others include Google (9%), Amazon (5%), Wells Fargo (4%), Chase (2%), LinkedIn (2%), Apple (2%), and Dropbox (2%).
Upped Their Game:
It used to be that phishers were an unsophisticated bunch. Now, bogus websites are hard for even experts to detect.
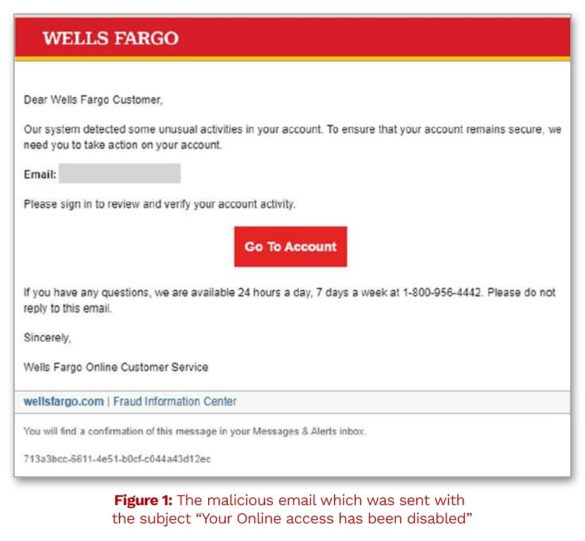
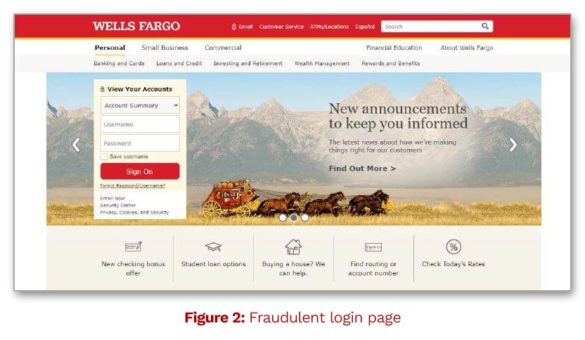
Consumers may receive phishing emails from banks they don’t even do business with. But it’s more believable when it’s their own bank, and the email looks exactly like the legitimate ones they’ve received in the past. In one example noted by Check Point Research, a criminal sent a scam email to a Wells Fargo customer, noting that their account had been disabled.
As noted, the pandemic caused phishing attacks to soar. “At the beginning of the crisis, businesses and citizens around the world took advantage of government-backed business loans and payment deferrals or ‘holidays’ from consumer banks and credit unions,” the Vade report states.
An interesting result of this is that as the world’s large economies return to normal, the “bill is coming due” for such deferrals.
“This is a significant weapon for phishers to wield against businesses and individual citizens who borrowed or deferred and could signal a continuance of the trend toward financial services phishing as payment moratoriums expire around the world,” Vade notes.
( Read More: Consumers Fear Bank Fraud More Than Death And Terrorist Attacks )
‘Dr HeX’ Nabbed, But Other ‘Rings’ Proliferate
Many of the attacks in the early days of the pandemic carried COVID-related themes related to relief funds, unemployment benefits, or PPP loans, Goutal points out. More recent scams have included messaging around vaccines. “People have been stressed about their businesses and paychecks, and they’re emotionally fragile. The criminals are taking advantage of that,” he says.
Criminals are also increasingly advanced in their attacks. Many now operate large phishing rings that function like a legitimate business, Goutal states. Highly sophisticated, these rings often go undetected for years. In early July 2021, Interpol and Group-IB apprehended a suspect in Morocco after two years of tracking him. “Dr HeX,” as he was known, impersonated online banking services and lured account holders to submit their account credentials and was involved in thousands of phishing schemes and other scams.
One new strategy phishers began using in 2020 was to embed more text into images to bypass security filters. These filters can quickly scan through text to validate emails, but it’s more difficult to do when the image is linked and not attached to the email. “You can’t filter it in real time,” says Goutal. You need to leverage computer vision techniques and it’s expensive.”
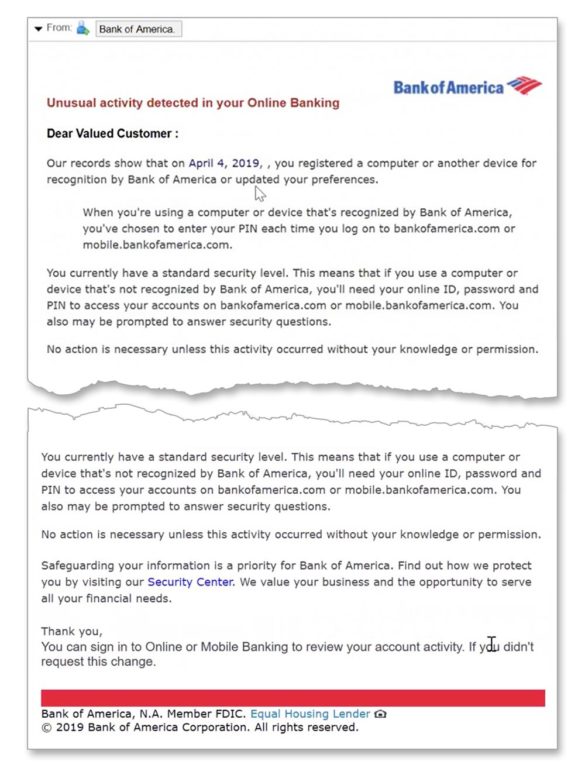
In another example of creative phishing, the criminals used security alerts to pull off the con. In the actual example below from a 2020 Vade report, the bogus Bank of America email warns the victim that a new device is being used in association with their bank account. As noted by Vade, the email cleverly doesn’t include the link until the end to ensure the target is “sufficiently primed.”

Fighting the Phishers
It’s easy to think that only fools fall for such scams, but that’s far from the case. In “spear-phishing” campaigns, criminals will go to great lengths to personalize and customized emails. One big target isn’t consumers, but financial institution employees, who can inadvertently reveal account information.
Start with Employees:
Financial institutions can’t control what emails customers open, but they can help ensure their employees aren’t duped.
Banks and credit unions can mitigate this risk with training and awareness. Brad Neumann, Senior Manager of Risk Management at CUNA Mutual Group, wrote in an article that employees should be the first line of defense with frequent social engineering and phishing training. “Reminders should regularly be made to not open suspicious emails, not click on links or open attachments contained in such emails, and to be cautious before visiting unknown websites,” Neumann states.
( Read More: Balancing Fraud Prevention and Customer Experience During Onboarding )
But even the best security on the institution’s end does nothing to protect consumers on the receiving end. Here are several ways that banks and credit unions can increase awareness.
Wells Fargo advises customers to never sign into their account through a link in a suspicious message. When in doubt, the best course of action is to open a fresh browser window, type in the web address and log into the account from there.
PNC Bank warns its customers that while it may occasionally ask them to reply to a text message, it will never ask customers to click on a link from a text. PNC notes common red flags of a possible phishing or “smishing” (SMS, or text, phishing) attack include:
- Misspellings
- Grammatical errors
- Creating a sense of urgency
- Requesting personally identifiable information
- Requesting user IDs and passwords
The American Bankers Association’s Banks Never Ask That campaign has consumer-facing information warning about phishing scams, and how to identify them. ABA notes that while consumers may be asked to verify confidential information when they call a bank, it is rarely the other way around.
Phishing emails often involve scare tactics, asks for confidential information, and direct the consumer to a link. The ABA site also offers a quiz where consumers can test their skills in identifying common bank-related phishing scams.